Layer 8 Hacking - Linking the OSI Model with the NIST Triangle
4.5 (260) · $ 12.50 · In stock
Layer 8 Hacking can be defined as hacking above and beyond the technical layers; hacking by targeting the user, the business processes, or the organization i

Cyber security breakdown: The OSI model
The OSI Model Explained: Handy Mnemonics to Memorize the 7 Layers
The Open Systems Interconnection model is a conceptual model that characterises and standardises the communication functions of a telecommunication or
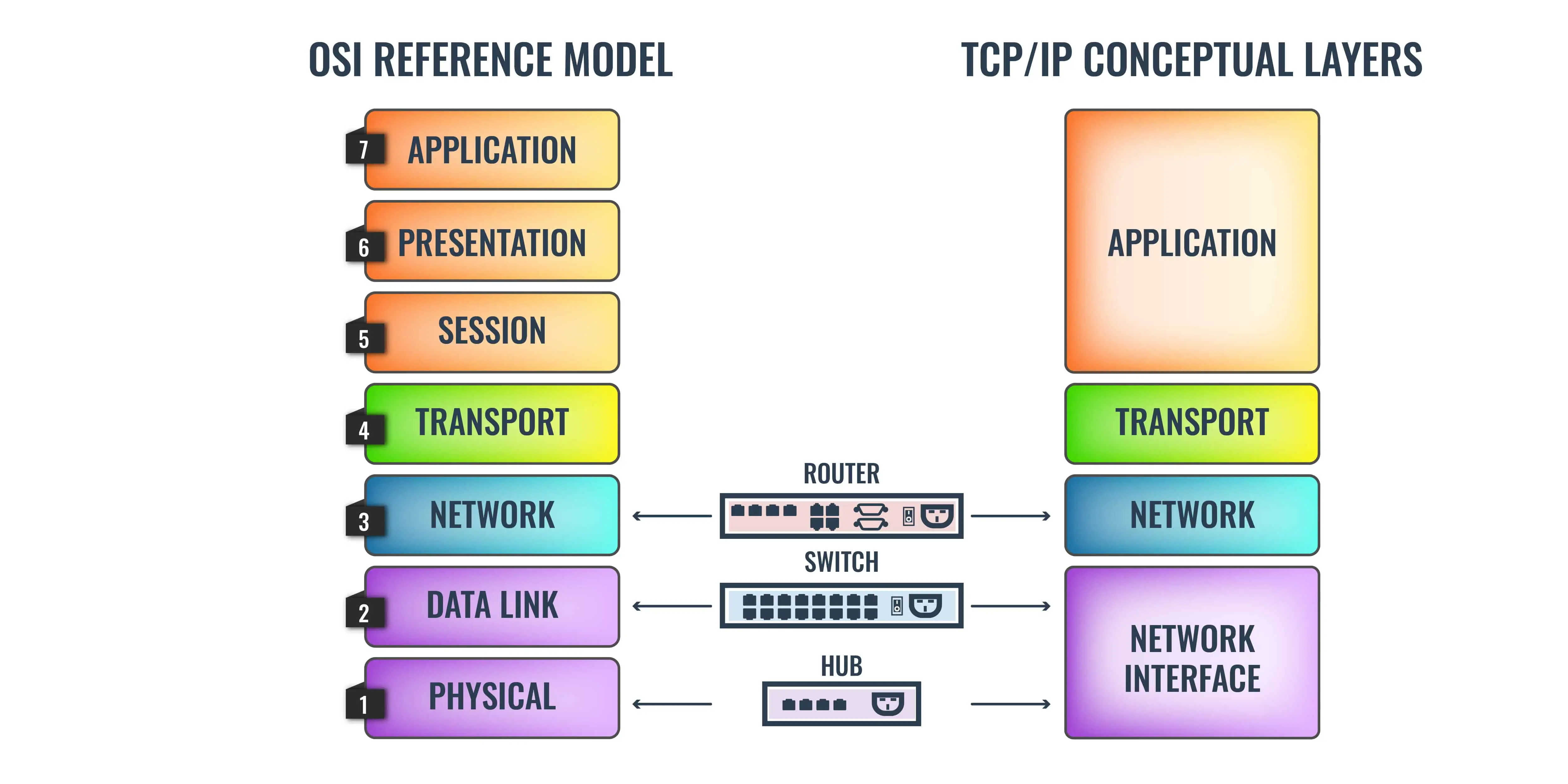
Cyber security - Hacker Networking Skills - OSI Model vs TCP/IP
NIST Zero Trust Architecture: Key Points to Learn
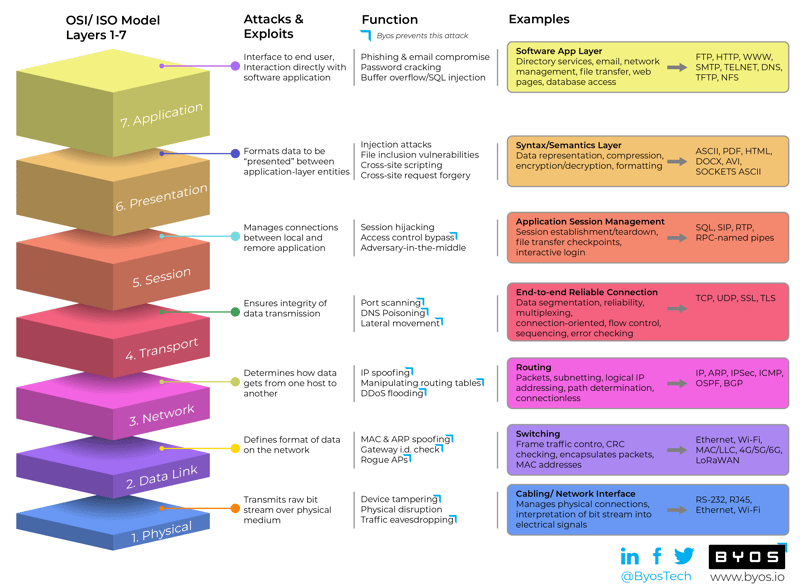
How Cyber Adversaries Attack Each of the OSI Layers 1-7

The OSI Model Explained in Easy Steps

OSI Reference Model Penetration Testing
Stateful Inspection - FasterCapital

8th Layer in OSI Model…. Twitter recently disclosed that its own

A survey of cyber security threats and solutions for UAV
Glossaries learnonline











