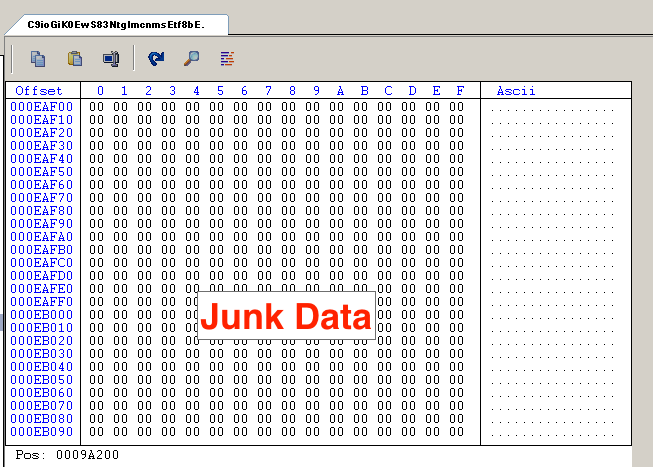
How Hackers Use Binary Padding to Outsmart Sandboxes
4.8 (361) · $ 20.00 · In stock
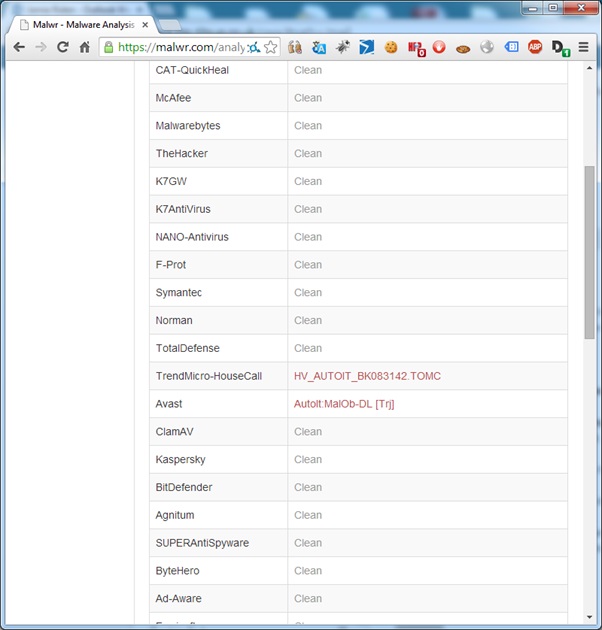
Quick and dirty binary analysis using sandboxes

Emre KISA على LinkedIn: How Hackers Use Binary Padding to Outsmart Sandboxes and Infiltrate Your…

Emre KISA on LinkedIn: If only i had a dollar for everytime i was asked for this 🙄

Roy Halevi (@royhalevi) / X

Misconfigured Airflows Leak Credentials from Popular Services

Intezer on LinkedIn: How Hackers Use Binary Padding to Outsmart

How can Advanced Sandboxing Techniques Thwart Elusive Malware? - Wiadomości bezpieczeństwa

CryptoClippy Evolves to Pilfer Even More Financial Data

Intezer on LinkedIn: How Hackers Use Binary Padding to Outsmart
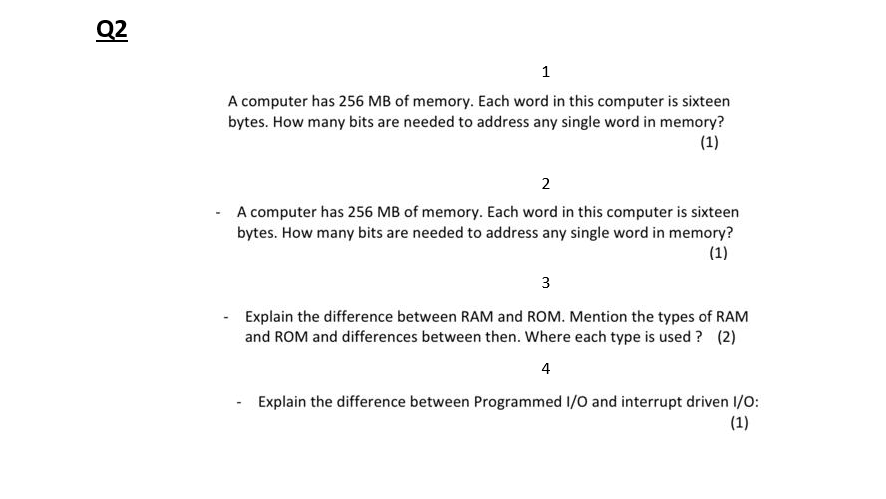
Solved Memory Address Is Always In Terms Of, 43% OFF
How Sandboxes Help Analysts Expose Script-Based Attacks

Top 10 Linux Server Hardening and Security Best Practices - Intezer

Misconfigured Airflows Leak Credentials from Popular Services

Intezer - Blog

How Hackers Use Binary Padding to Outsmart Sandboxes